Internet access makes it easy to access the world through a number of services. Sit in front of your friends and family. You can see the information about the bridge and the bridge, but also the map. m & agrave; Your account Can be entered in any of the fields. you do not know before. Therefore, the protection of the system; a problem we have to be aware of. People Introduce FireWall to solve the problem.
Internet access makes it easy to access the world through a number of services. Sit in front of your friends and family. You can see the information about the bridge and the bridge, but also the map. m & agrave; Your account Can be entered in any of the fields. you do not know before. Therefore, the protection of the system; a problem we have to be aware of. People Introduce FireWall to solve the problem.
FireWall l & agrave; g & igrave; first
The term FireWall c. Derived from a design technique in order to prevent, limit fire. In the latest news, FireWall, A networked technique to prevent unauthorized access to protected internal data sources as well as to restrict access to and retrieval of data. o the system of some of the information is not expected.
Internet FireWall l & agrave; a set of devices (including hardware and software) between an organization's network, a company, or an intranet; Internet:
(INTRANET & nbsp; - & nbsp; FIREWALL - & nbsp; INTERNET)
In some cases, can be set up in an internal network. c & ocirc; set up an anonymous domain V such as m & ocirc; Underneath is a local area network that uses & nbsp; Firewalls to prevent unauthorized use of your computer. network downstairs.
 |
Function
FireWall decides which services are accessible from outside the network, people from outside the US and from outside the US. B & N services; All of these services are accessible by the people in your area.
FireWall stub
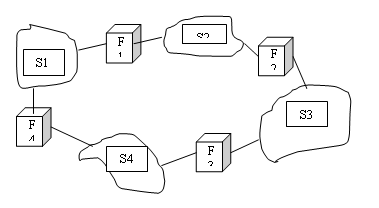
FireWall includes:
One or more host systems connect to a router or cradle. router function.
C & rsquo; security system running system Often, c. Authentication, Authorization v & agrave; to & accounting (accounting)
The most important part of FireWall
A FireWall consists of one or more of the following:
Packet filtering (packet-filtering router).
Application-level gateway or proxy & nbsp; server.
+ Circuite level gateway.
FireWall protects your computer from viruses. first
Basic task of FireWall l & agrave; Protect the following issues:
Data: Messages need to be protected due to the following:
- & nbsp; Protect.
- & nbsp; Ute ute .
- & nbsp; Make timely.
The system is in danger.
+ & nbsp; The reputation of the company that owns the information you need to protect.
FireWall protects against viruses. first
FireWall protects against unauthorized attacks.
+ Direct tones:
& nbsp; & nbsp; & nbsp; & nbsp; & nbsp; & nbsp; & nbsp; & nbsp; & nbsp; First and foremost, D & C; direct passwords. It has been through the use of the User password with some user information such as age, address, age, address, etc. & hellip; In combination with the library created by the creator, the attacker uses his / can & dquo; be your password. In some cases, the ability to Up to 30%. V For example, The password for the Unix operating system. & n; Crack.
& nbsp; & nbsp; & nbsp; & nbsp; & nbsp; & nbsp; & nbsp; & nbsp; & nbsp; C & # 039; t second l & agrave; Use the error of the application program. Attribution-Noncommercial- is used from the first attack. is still to gain access (c) be authorized by the system administrator.
+ Eavesdropping: C & oate; You can know the password, which is used by your network operator through a program that allows you to send and receive network communications (NICs). The data packets transmitted over the network.
+ & nbsp; Forged IP address.
+ V effect The system's function (deny service). & Ldquo; This is a great way to get started. To set up your system, Performs the m & agrave function; n & oacute; designed. The type of damage that can be prevented by the means of organizing attacks is also important. The means by which to work and to work. access to network information.
+ System administrator error.
+ Human Factors with the Home & r & otilde; The importance of system security makes it easy to disclose important information to hackers.
Today, the level of hackers has improved, while the number of hackers has increased. The network is still slow to process. The vulnerability of Microsoft. I have asked the network administrator to Good knowledge of network security. It can keep the system up to date. For the people They do not know how to set up a firewall for themselves, but they understand that. the importance of information security for each & nbsp; Educate yourself for some of the simplest ways to hack a hacker. Problem l & agrave; & yacute; when c. & yacute; How to play the game? The annealing ability will be higher. & nbsp;